Three-Tier Architecture
Introduction
The AWS 3-tier architecture consists of a Presentation layer hosted in public subnets for routing and frontend delivery, an Application layer in private subnets running business logic, and a Data layer also in private subnets for secure storage and database access—all orchestrated across multiple Availability Zones for high availability and fault tolerance.
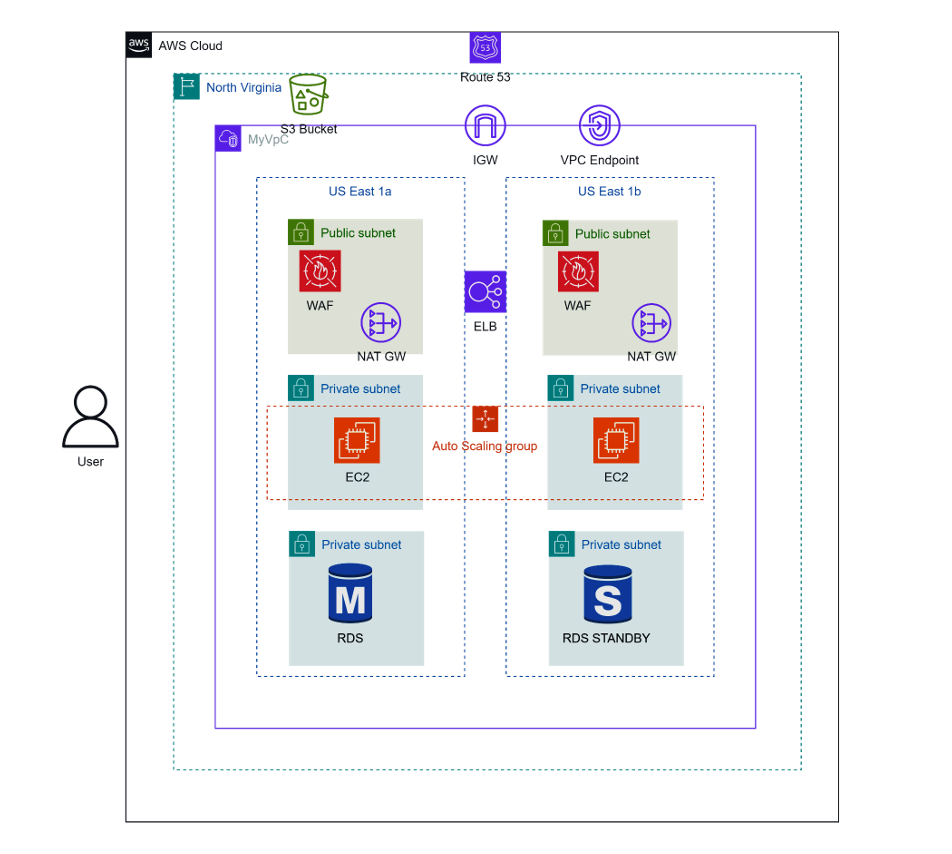
Architecture Overview
- Route 53:
- AWS-managed DNS service that routes domain names to AWS resources.
- Supports global routing policies based on latency, geolocation, or failover strategies.
- Commonly used to direct traffic to CloudFront distributions or Application Load Balancers (ALB).
- Internet Gateway (IGW): Connects the VPC to the internet, enabling public subnet traffic.
- VPC Endpoint: Allows secure, private access to services like S3 without traversing the public internet.
- Elastic Load Balancer (ELB): Distributes inbound traffic across multiple EC2 instances in different AZs.
- Auto Scaling Group: Automatically adjusts EC2 instance count based on demand.
- Web Application Firewall (WAF): Adds protection against common vulnerabilities like SQL injection or XSS.
- NAT Gateway: Lets private instances access the internet for patches and updates.
- EC2: Hosts application logic in private subnets, linked to Auto Scaling for resilience.
- RDS: Managed private relational database instance.
- RDS Standby: Replica in another AZ for failover and continuity.
- S3 Bucket: Durable object storage for backups, logs, and static assets.
Summary
This architecture exemplifies AWS best practices by enforcing strong security across layers, ensuring fault tolerance with multi-AZ deployment, and scaling resources elastically to meet demand. It's a resilient, secure, and cloud-native solution suitable for modern web applications.